


2024 Upfort Phishing Attack Report
Understanding the ins and outs of phishing attacks including a company's level of preparedness to protect against different attacks, the most at-risk states, and the most cyber-resilient industries.
Table of Contents
Phishing attacks are the most common cyber attacks against individuals and organizations. According to security researchers, 91% of cyberattacks against businesses are launched via email. On average, 3.4 billion phishing emails are sent every day, often masquerading as messages from trusted sources.
Breaches at large corporations dominate the headlines, but cybercriminals are increasingly shifting their focus to small and medium-sized businesses (SMBs). SMBs are, in fact, 3x more likely to be targeted than enterprise companies due to:
- Fewer cyber defense resources
- More relaxed posture owing to the misguided notion they’re “too small to attack”
- Inadequate security awareness training for employees
Studies have repeatedly shown that the most important security step companies can take is training employees–the first line of defense–to recognize tell-tale signs of a phishing attack.
Upfort’s Cyber University provides enterprise-scale security awareness training to businesses of all sizes. Even better, it ensures preparedness with robust phishing simulation functionality to auto-generate mock phishing emails and provides insights about how employees responded.
In this report, we’ve gathered a year’s worth of simulation data to illustrate the current state of phishing affairs. Using anonymized collective data from real users, we’ve surfaced the relative “effectiveness” of different attacks, the geographic areas most prone to being phished, and industries that were most effective at repelling attackers.
The following report uses anonymized collective data from more than 125,000 phishing simulations run by our customers between Q3 2022 and Q3 2023.

How Upfort Phishing Simulations Work
Upfort’s AI-powered defenses are continuously updated with global cyber claim data supplied by our insurance partners. This exclusive dataset allows our team to simulate the latest phishing methods across two main categories:
- Credential-based attacks: In which attackers attempt to steal credentials by pretending to be a trusted source
- Attachment-based attacks: In which users are tricked into downloading and opening an infected file that they mistakenly believe to be innocuous
All emails come “from” either the internal colleague or from a known third-party company (Uber, etc.), however, an examination of the email address or metadata would reveal none of these messages are actually from whom they claim.

If a team member is fooled by a simulated attack, the system provides real-time alerts informing them of their misjudgment. Members who download attachments are sent automated emails notifying them of their potentially dangerous action, while those who submit credentials are redirected to an informational landing page similar to the one shown below.

Upfort’s platform makes it simple for businesses to launch simulated phishing attacks against their team with just a few clicks—no IT or security specialty needed. Admins receive real-time data on the success of those test attacks, which they can use to fortify their human defenses.

Phishing attack types, by the numbers
Within the scope of this dataset, attachment-based (AB) phishing emails were, by far, more likely than credential-based (CB) emails to be opened, and to result in a dangerous action.
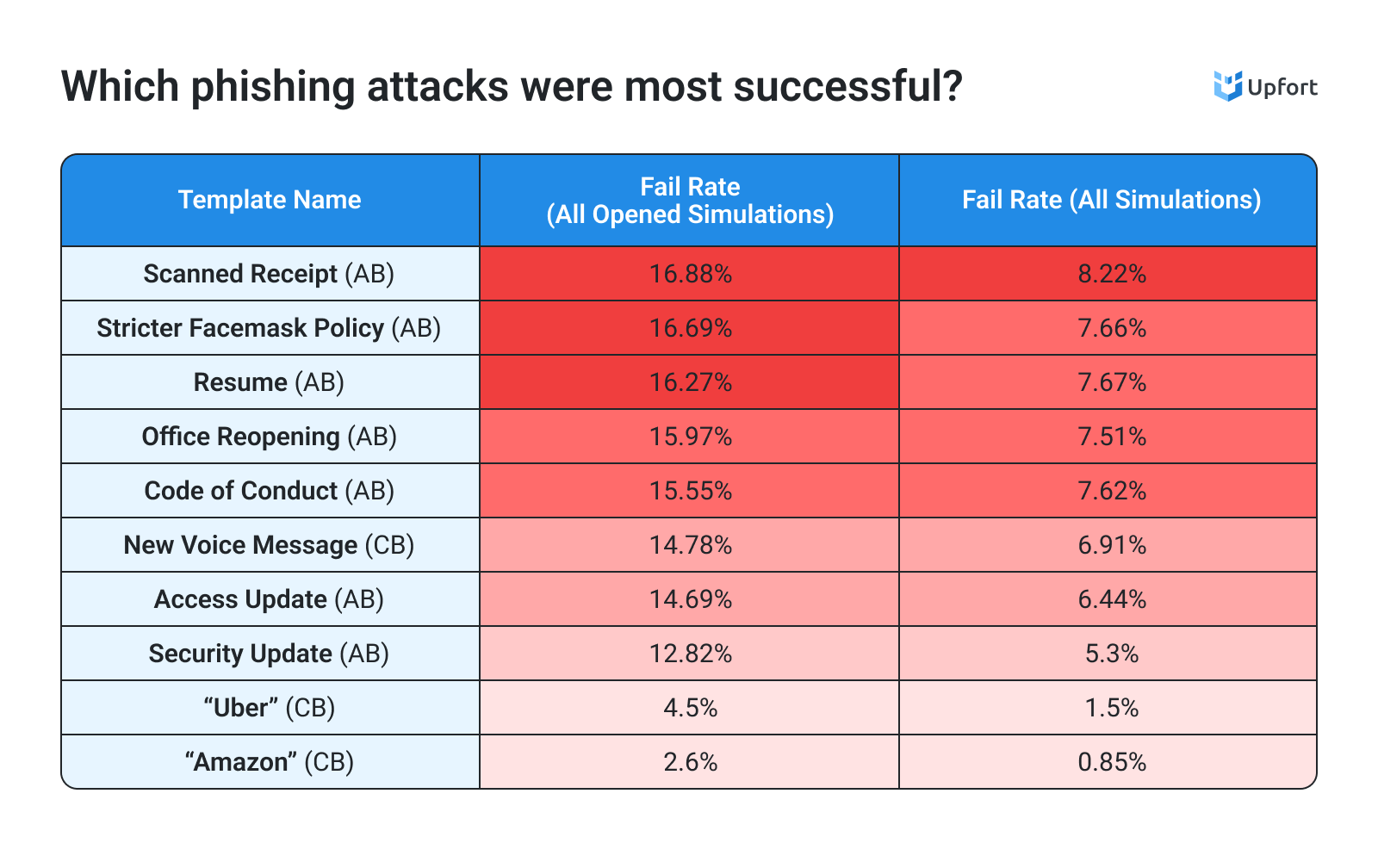
A “scanned email” AB email had the highest overall fail rate (8.22%) and the highest rate among opened sends (16.88%). The “success” of this simulated attack could be attributable to the ostensible legitimate nature of the message and the need to open the attachment of such a message.
It’s interesting to note that two of the top four most successful phishing simulations (by fail rate among opened submissions) were associated with COVID quarantines (“Stricter Facemask Policy” at 16.69% and “Office Reopening” at 15.97%). These topics were topical during the survey period (2022-23) and why you would expect them to be represented in the greater phishing landscape, and therefore reflected in Upfort’s emails. Their inclusion is very illustrative of how phishers tailor and evolve their attacks around world events to illicit action.

Users were generally better at discerning mock-CB attacks from legitimate sources (messages from Uber and Amazon, for example, had comparatively low open and fail rates). There could be many reasons for this relative lack of success of the CB emails—notably simulation emails were sent to work accounts rather than the personal ones, leading most users to rightly disregard these messages.
Still, nearly 1-in-20 users who opened the “Uber” email went on to provide their log-in credentials to the “cybercriminals.” Accidentally granting criminals access to a third-party service account can be annoying, invasive, and potentially expensive for individuals, but it can also place employers at risk. Too often, people reuse the same password across multiple services—both in their personal and work lives—so, if a criminal cracks a personal service, they often can crack professional ones as well. More insidiously, criminals can glean personal information from infiltrated third-party services to conduct highly targeted social engineering attacks against other team members.

The least and most phishable industries
Below are the top 20 industries among the testing population (only including companies with known verticals, and among industries with >1% of the testing population).

It’s perhaps not surprising to see technology companies listed as the least “phishable” sectors—there’s an inherent awareness of cyber issues among tech workers, which may influence management to implement additional security layers, such as inbox threat scanning. Surprisingly, Not-for-Profit Organizations scored the third-lowest fail rate on the list (1.9%), which is all the more impressive in that they were the second-largest population pool.
At the other end of the phishable spectrum are three sectors that were frighteningly vulnerable considering the personal nature of the data they process and the impact of the services they provide. Medical/Healthcare Related Services came in as the most phishable sector with a 12.9% overall fail rate–which translates to 1-in-8 of all simulated emails resulting in a fail.
Government Agencies came in third overall (10.8%) and had the highest fail rate when it came to AB attacks (10.76%), while local municipal agencies weren’t far behind with an uncomfortably high 9.2% fail rate. This comparatively high failure rate among government organizations is all the more worrisome as researchers have observed a notable uptick in phishing attacks on government workers in recent years.

Phishability, a state-by-state breakdown
Below are the 15 US states sorted by which one was most phishable. Note: we’ve limited the scope of the report to include states with similarly large testing populations.

There’s little regional difference between phishing rates (i.e., we can’t definitively say the southeast is definitively more phishable than the northwest, for example). But there are some interesting patterns hidden in the data: In every state but three, attachment-based (AB) fail rates were higher than credential-based (CB), and two of those inverted states, Washington and Missouri, are at the top of the overall fail list (22.3% and 17.9% respectively).
Missouri, in particular, stands out because it scored near the middle of the pack for AB fail rates (5.60%), but led the study in regards to CB fails (12.32%). Poor Washington state had, in addition to the second-highest CB fail rate (11.67%) the highest AB fail rate by far (10.59%)—more than three full percentage points above the next highest AB fail rate (Wisconsin with 7.76%).
And hats off to Georgians who earned the lowest overall fail rate (2.0%) by having the lowest AB fail rate (1.12%) and fourth-lowest CB rate (0.77%).
Conclusion
Phishers are constantly changing their tactics, so it’s important to arm your workforce with knowledge and tools. This threat will only become more daunting as phishers make use of emerging generative AI tools to craft highly specific messaging at scale. You need a partner to take on this evolving threat.
Upfort was designed to deliver enterprise-grade protections to organizations of all sizes in the form of expert-designed cyber awareness training alongside advanced, AI-powered defenses. Interested in beginning your cyber journey? Sign up for a free cybersecurity risk assessment and subscribe to our business-focused security newsletter. Want to learn more about how Upfort can help your organization? Schedule a live demo with one of our in-house experts.
Also, check out our 2024 Phishing Attack Report infographic.


